Utilize Cloud Provider for Enhanced Data Safety
In today's electronic landscape, the ever-evolving nature of cyber risks demands a positive approach towards protecting sensitive information. Leveraging cloud solutions offers an engaging remedy for companies looking for to strengthen their information security measures. By handing over reliable cloud service companies with data administration, services can use a wide range of safety features and advanced modern technologies that strengthen their defenses against destructive stars. The question emerges: just how can the usage of cloud solutions transform information safety and security methods and offer a robust guard versus possible vulnerabilities?
Relevance of Cloud Safety
Making sure durable cloud safety and security steps is critical in protecting sensitive data in today's electronic landscape. As companies progressively depend on cloud services to save and process their information, the requirement for solid safety protocols can not be overemphasized. A breach in cloud protection can have serious consequences, varying from financial losses to reputational damages.
One of the key reasons that cloud safety and security is crucial is the common obligation design used by most cloud company. While the copyright is accountable for protecting the infrastructure, consumers are accountable for securing their information within the cloud. This division of responsibilities highlights the relevance of executing robust safety steps at the individual degree.
Moreover, with the expansion of cyber dangers targeting cloud settings, such as ransomware and data breaches, organizations need to remain watchful and positive in mitigating risks. This involves consistently upgrading security procedures, checking for suspicious tasks, and enlightening employees on finest methods for cloud safety and security. By focusing on cloud security, organizations can better secure their delicate data and maintain the trust of their clients and stakeholders.
Information Encryption in the Cloud
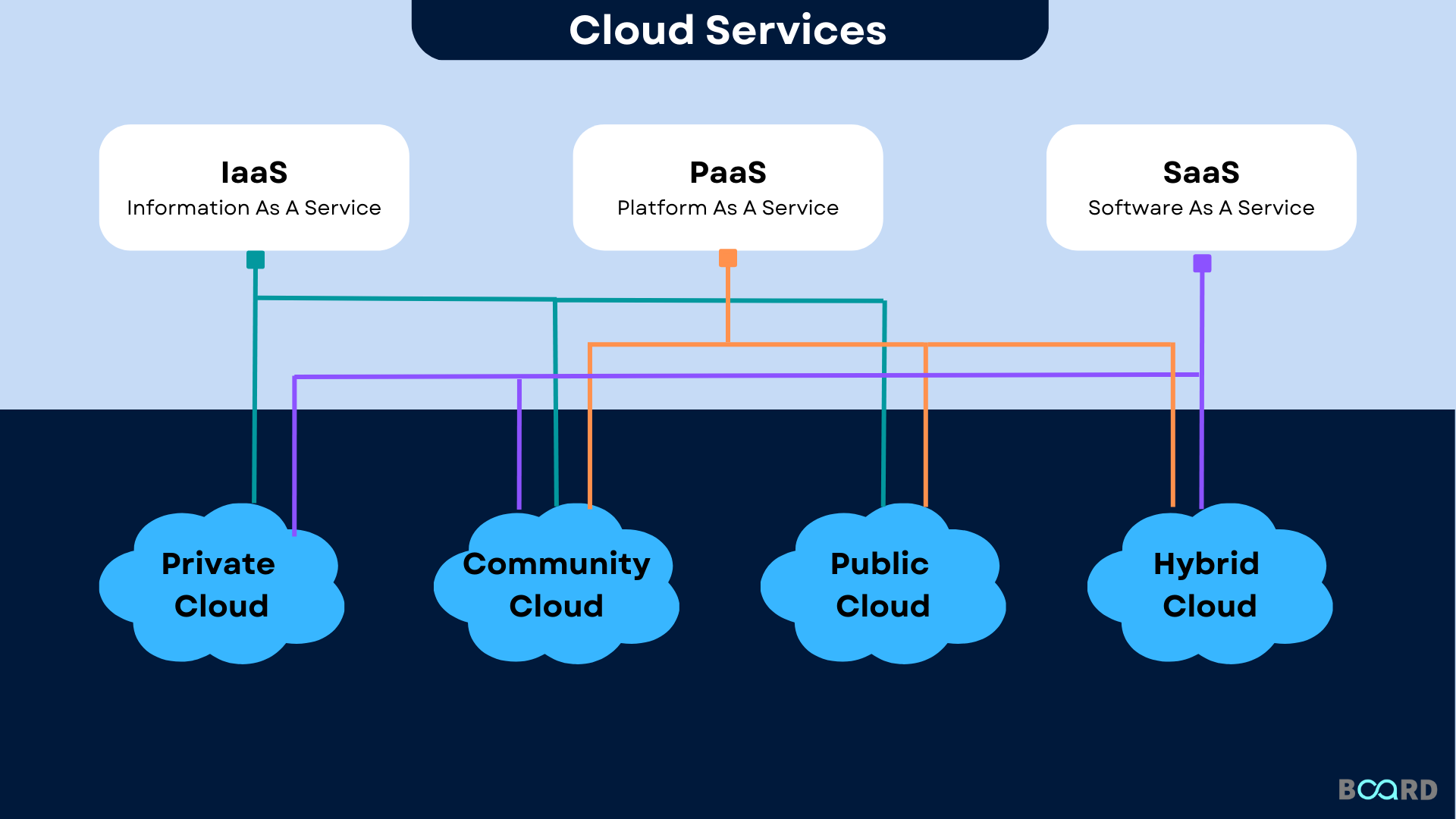
Security in the cloud generally entails making use of cryptographic formulas to clamber information into unreadable styles. This encrypted information can only be decoded with the matching decryption trick, which adds an added layer of safety. Additionally, several cloud provider offer security systems to secure data at remainder and in transit, boosting general data security. Implementing durable encryption practices together with other security steps can dramatically reinforce a company's protection versus cyber threats and secure useful details saved in the cloud.
Secure Information Back-up Solutions
Information backup services play an essential duty in making certain the strength and protection of information in case of unanticipated occurrences or information loss. Safe information backup options are crucial parts of a durable information safety and security technique. By frequently supporting information to protect cloud servers, organizations can mitigate the threats linked with information loss because of cyber-attacks, hardware failures, or human error.
Implementing secure information backup options entails picking trustworthy cloud solution suppliers that use file encryption, redundancy, and data honesty actions. Security ensures that data remains protected both en route and at remainder, guarding it from unauthorized gain access to. Redundancy mechanisms such as information duplication across geographically spread servers aid avoid full see data loss in situation of web server failures or all-natural catastrophes. Additionally, information honesty checks guarantee that the backed-up data continues to be unchanged go to this site and tamper-proof.
Organizations ought to develop automatic backup timetables to ensure that data is regularly and effectively supported without hand-operated treatment. When required, regular testing of data remediation processes is also vital to assure the performance of the back-up solutions in recovering information. By purchasing safe and secure data backup services, organizations can enhance their data protection posture and reduce the influence of possible data breaches or disturbances.
Duty of Accessibility Controls
Executing rigid access controls is necessary for keeping the safety and security and integrity of sensitive info within organizational systems. Access controls serve as a vital layer of protection against unauthorized access, guaranteeing that only accredited people can see or manipulate delicate information. By defining who can accessibility certain resources, organizations can restrict the danger of data breaches and unapproved disclosures.

On a regular basis updating and evaluating accessibility controls is vital to adapt to business adjustments and advancing safety hazards. Continual tracking and bookkeeping of gain access to logs can help spot any kind of questionable activities and unapproved access efforts immediately. Overall, durable access controls are basic in protecting delicate info and mitigating safety risks within business systems.
Compliance and Laws
Frequently ensuring conformity with relevant guidelines and criteria is necessary for organizations to maintain data protection and privacy measures. In the world of cloud solutions, where data is often saved and processed on the surface, adherence to industry-specific policies such as GDPR, HIPAA, or PCI DSS is crucial. These laws mandate certain information managing practices to safeguard delicate info and make certain customer privacy. Failure to abide by these regulations can lead to extreme charges, consisting of penalties and lawsuits, damaging a company's track record and depend on.
Many companies provide encryption capabilities, access controls, navigate to these guys and audit trails to aid organizations meet data protection standards. By leveraging certified cloud services, companies can improve their information safety posture while fulfilling regulatory commitments.
Final Thought
To conclude, leveraging cloud services for enhanced data security is necessary for organizations to protect delicate information from unapproved access and possible breaches. By applying durable cloud safety and security protocols, consisting of information file encryption, protected back-up remedies, gain access to controls, and conformity with guidelines, companies can gain from sophisticated protection steps and knowledge used by cloud company. This assists minimize risks efficiently and makes sure the discretion, integrity, and accessibility of information.

Information backup solutions play a critical duty in making certain the durability and safety and security of data in the occasion of unforeseen events or information loss. By consistently backing up information to protect cloud servers, companies can alleviate the risks linked with information loss due to cyber-attacks, hardware failings, or human error.
Executing secure information backup services entails selecting reliable cloud solution companies that offer security, redundancy, and data integrity actions. By spending in safe data backup options, companies can boost their data protection pose and decrease the effect of possible data violations or disruptions.
Comments on “Cloud Services - Transform Your Digital Infrastructure”